Successful layering
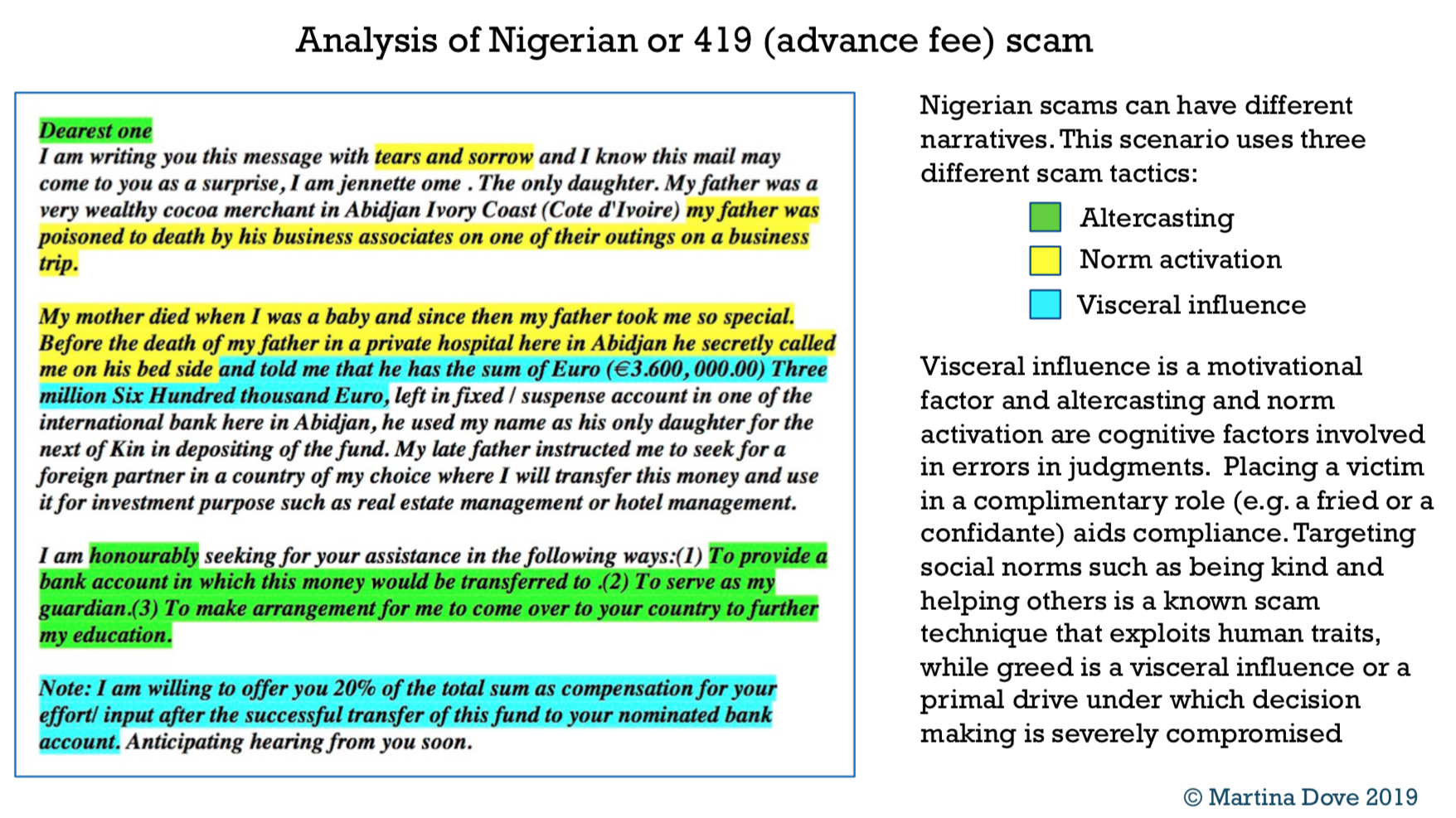
/Scams can be extremely sophisticated, yet for many people, a typical scam is a Nigerian prince asking for help to launder money or a desperate, and dare I say naive, scammer that was talked into holding ‘I can’t believe it’s not butter’ sign, hoping this would get them some funds. But the reality is much darker. Good scammers are very good at psychology and often design frauds by layering different fraud techniques, all designed to complement each other for greater success. For example, scams that evoke visceral influence (fear, panic or greed) will usually have time limits attached to them also (e.g. offer expires, you have 24 hours etc.). This is to ensure that the potential victim has no time to regain composure. Under visceral influence, careful deliberation is compromised and we tend to focus on superficial things, like the size of the reward, attractiveness of the offer or even on the scammer, many of whom are polished, charming and will appear trustworthy. Any inconsistencies will be disregarded in favour of these superficial cues, because when one is under the visceral influence, they are likely to focus on goals associated with that influence. This is why you are always told not to go shopping for groceries hungry and it’s equally true of acting on anything when intense fear or excitement has been evoked.
Scams that appeal to social norms, often use altercasting too. Altercasting is another persuasive technique, where a perpetrator will put a victim in a specific role that is congruent with their goals. For example, I have seen advance fee scams that use narratives where either an orphan girl, a widow or even a pastor appeals for help (social norms) and the victim is placed in a role of a friend or a confidante, where a perpetrator will trust the victim with confidential or deeply personal information before asking for funds down the line. By that time the victim has been acting as a friend or an advisor and this role is likely to help facilitate the fraud, because they will be more likely to help.
Scammers often layer persuasion techniques for greater impact.
In conjunction with other individual factors, these techniques can be very effective.
Other factors also come into play. Different circumstances, for example, have been known to influence compliance in certain scam situations. Or certain individual characteristics, such as lack of vigilance or impulsivity. For example, if you are down on your luck, looking for work and you are running out of money, you will be more likely to take risks and consider financial opportunities that don’t look very sound. You may be more likely to concentrate on potential rewards instead of any negatives associated with high return investments. If you are also more compliant in general, it is even more likely that, when persuaded to do so, you will decide to go along with something you have some reservations about. Of if you are more impulsive, you may act quickly, without allowing the time to think about your decision. All of these factors combine (or layer) to produce a unique vulnerability score.
Many frauds are still relatively simple. Badly constructed phishing email that will bring a smile to your face, for example, but many are far from simple. It all comes down to how good the scammer is and how motivated they are in developing a highly credible looking, psychologically designed frauds that create situations that can be highly persuasive, and how they go about executing them. The more effort they invest, the more lucrative the venture will be, so it’s good to be vigilant and not underestimate what fraudsters are able to do by concentrating only on badly designed scams that are easy to spot.